How Cape Encrypt Works
cape encrypt is a command to encrypt data which can only be processed by Cape Functions that you deploy. With cape encrypt you don’t need to manage keys, implement encryption protocols, or worry about the security of your data.
An example of encrypting data with Cape:
cape encrypt 'Hello World!'
cape:NuBgifA+nWAGxC4CDonkmjfMbOBlkbjtZrqwkZwJ1idKub1p6TnY+2CfPDUfSm/yFbaHWwfRCAXpY8i1nv6DeJ8yMEzhnRbANNkfShP6fRX05VaNh5idrGKiXattppXMot3233yFtUK+7MR1CcScOH1YplHL8jFIJYqEF8lMS+YGphijqiL8sIwP4kyiPRx+QFL9AEL5I53/CFG1eXFkzcprSrk7jzALaUZ2frsVz8pznP6fOOmLFKvX1Z5OrssEax7cNVwrSLG3mV5t8X+tF6/Y9Xl/blMEhlHL690VUmJHyg5w9JDaIyBD2af54ESV8v9W9ZXRGSyyya0GGBpQjmrOJfSATxmW7B8ZDfLk2wPOLYBHMWAiWoQswLAnXWhexohxe2Y3/D8ESBEM3KmamQecFmFDVsgaTTVdb9wPGSJY8bLwDXLPg9pS3BbXouRddnfh3O15BqA/WYwYgQfLEX7cXeqiTpQql6aIjvqX5u8D312xtmVJmObBdYZuPKdlOSF5cEaAYxrCSEeY4yTjvEiKirQeIPh00OPLrvLk8jt6vQLe22y8KRziOJv6vBuTqZTUQRtpDSy25sCt3XMqDSZikZvHbgCEFlFk4kaBXl0AiYcROA0ItpYbD/cy+rIyC3b/8uhNXVN/G/BtxmWWtAzvdgFhPElSOF8vK1fwTSjYRBEsLP46H5vRIh7zDnt8lZ362VkRcxX6OQ7BWr/RTwCaGnu1DQJR
The result is prefixed with cape: so that it’s easily identifiable as Cape encrypted data when you store it or share it.
Encrypting Data with Cape
The first time you call cape encrypt, Cape’s secure enclave will generate a key pair within KMS (AWS Key Management Service) which is unique to your account. The key pair contains a public key (your Cape Key) for encrypting and a private key for decrypting. The key pair is created with an immutable policy that prevents any user or any systems from decrypting with the private key, except for Cape’s secure enclave. The private key itself can never leave the KMS. Your Cape Key is sent securely from the enclave to the client in an attestation doc which is signed by the enclave.

The Cape client then verifies the attestation document, checking the signature, and the nonce (How Cape’s Attestation Works). If the attestation handshake is verified, your Cape Key is considered safe and can be stored and shared with other developers. Next, The Cape client will extract your Cape Key from the attestation document, and begin encrypting the data with an envelope encryption following the sequence below:
- Generates a random 256 bit data encryption key (DEK).
- Encrypts the input data with the DEK using AES 256.
- Encrypts the DEK with your Cape Key using RSA 4096.
- Combines the AES encrypted data and the RSA encrypted key to create the encryption envelope.
- Base64 encodes the encryption envelope, prefixes it with
cape:, and displays it to the user.

It’s important to note, that the encryption process happens offline on your local machine. This means that your data never touches the network. The only network is the initial request to download your Cape Key, which only happens the first time.
After the first call to cape encrypt, the Cape Key is cached on your machine, so subsequent calls to cape encrypt do not require any network. This means you can cape encrypt large amounts of data quickly and efficiently. In addition, cape encrypt works in scenarios with no network at all. For example, you could cape encrypt local data behind a firewall to secure it before storing it in the cloud. Your Cape Key can be shared and used anywhere for encryption. Keep in mind, that data can be Cape encrypted anywhere by anyone, and it can only ever be processed within Cape’s secure enclave.
Using Cape Encrypted Data
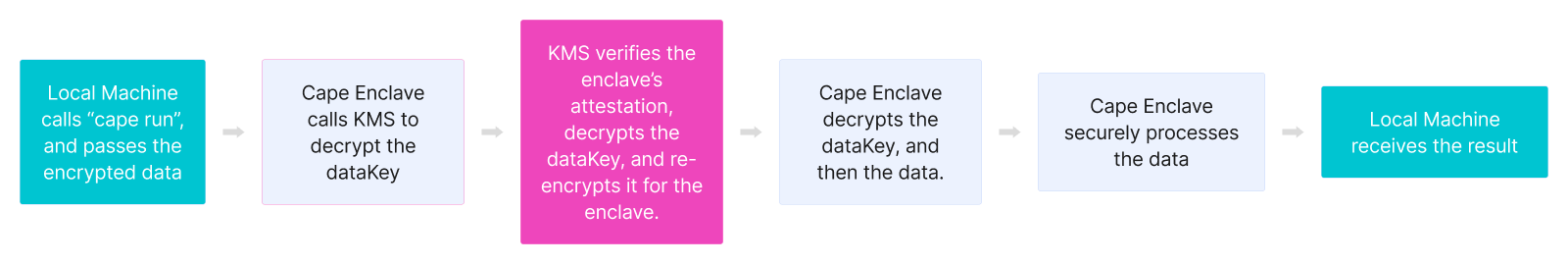
When it’s time to run a function, you can pass Cape encrypted data (prefixed with cape:) as a regular input, without any change to your functions. Cape’s secure enclave will automatically identify the input by the cape: prefix and decrypt it. Remember, this decryption happens within Cape’s secure enclave, which is a blackbox (How Cape’s Enclave Works).
The decryption relies on a call to kms:decrypt which will RSA decrypt the data encryption key (DEK) directly within KMS (remember, the private key used for decryption can never leave KMS). The KMS will only accept the kms:decrypt request if it successfully verifies the enclave’s attestation document. The resulting plaintext DEK is then re-encrypted by KMS with a public key provided by the enclave in the attestation document (How Cape’s Attestation Works). The encrypted DEK is returned to the enclave.
Now, only that specific and unique enclave instance has the private key to decrypt the DEK. The DEK is RSA decrypted, and the data is AES decrypted using the DEK. Cape’s secure enclave can now process the data securely as an input to your Cape Functions (How Cape Run Works). The decryption process is outlined in the sequence below:
- KMS: RSA decrypts the data encryption key (DEK) with the KMS’ private key.
- KMS: RSA encrypts the DEK with the enclave’s public key.
- Enclave: RSA decrypts the DEK.
- Enclave: AES decrypts the data.
- Enclave: Securely processes the data.
An example of a Cape encrypted input:
cape run sentiment-analysis cape:NuBgifA+nWAGxC4CDonkmjfMbOBlkbjtZrqwkZwJ1idKub1p6TnY+2CfPDUfSm/yFbaHWwfRCAXpY8i1nv6DeJ8yMEzhnRbANNkfShP6fRX05VaNh5idrGKiXattppXMot3233yFtUK+7MR1CcScOH1YplHL8jFIJYqEF8lMS+YGphijqiL8sIwP4kyiPRx+QFL9AEL5I53/CFG1eXFkzcprSrk7jzALaUZ2frsVz8pznP6fOOmLFKvX1Z5OrssEax7cNVwrSLG3mV5t8X+tF6/Y9Xl/blMEhlHL690VUmJHyg5w9JDaIyBD2af54ESV8v9W9ZXRGSyyya0GGBpQjmrOJfSATxmW7B8ZDfLk2wPOLYBHMWAiWoQswLAnXWhexohxe2Y3/D8ESBEM3KmamQecFmFDVsgaTTVdb9wPGSJY8bLwDXLPg9pS3BbXouRddnfh3O15BqA/WYwYgQfLEX7cXeqiTpQql6aIjvqX5u8D312xtmVJmObBdYZuPKdlOSF5cEaAYxrCSEeY4yTjvEiKirQeIPh00OPLrvLk8jt6vQLe22y8KRziOJv6vBuTqZTUQRtpDSy25sCt3XMqDSZikZvHbgCEFlFk4kaBXl0AiYcROA0ItpYbD/cy+rIyC3b/8uhNXVN/G/BtxmWWtAzvdgFhPElSOF8vK1fwTSjYRBEsLP46H5vRIh7zDnt8lZ362VkRcxX6OQ7BWr/RTwCaGnu1DQJR
69.46% Positive
Building Secure Apps With Cape
This unique combination of cape encrypt and cape run gives you a simple interface to build and deploy apps backed by secure enclaves and strong encryption. With cape encrypt you don’t need to manage keys, implement encryption protocols, or worry about the security of your data. cape run abstracts you away from the need to deploy and scale secure enclaves, manage cryptographic attestation, or worry about the security of your code in the cloud. Combining these two features, you can quickly build apps that encrypt, securely store, and securely process data.
Pickup your security superpowers: Getting Started with Cape
