Cape Run
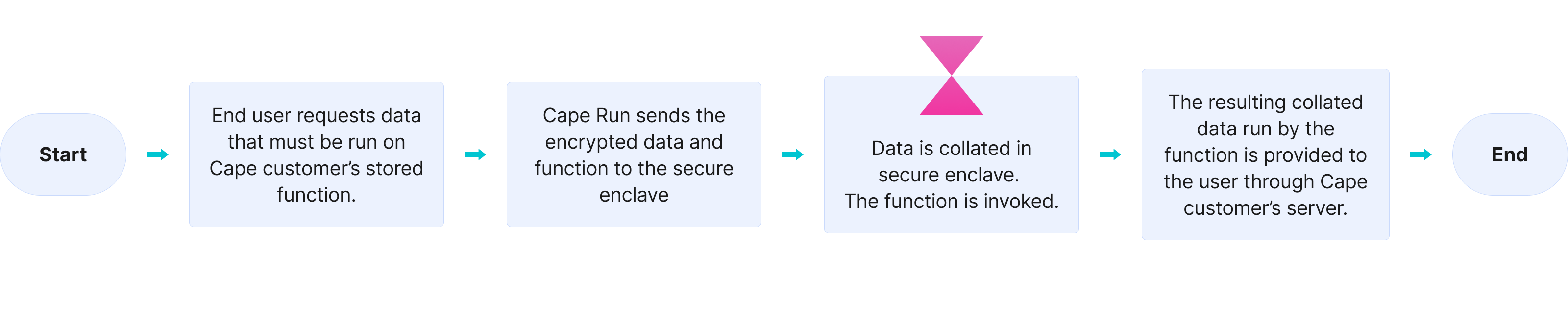 cape run invokes a deployed function.
cape run invokes a deployed function.
The same encryptions that happen during the cape deploy process are repeated during Cape Run, meaning that the function and data are both kept secure during the entire Cape Run process. Namely, cape run sends encrypted data and function for processing in a secure enclave where RSA decrypts Data Encryption Key and AES decrypts the data to only be securely processed in that secure enclave.
Once the results are returned, the enclave instance is destroyed so no data is saved.